In brief: If you’re going to visit websites that host pirated video streams, you’d better be willing to accept the risks. That’s something owners of the one million devices affected by a malware campaign originating from these sites might not have considered.
Microsoft writes that its threat analysis team detected a large-scale malvertising campaign that impacted nearly one million devices globally in December 2024.
The company traced the attack back to two illegal streaming websites – movies7 and 0123movie – embedded with malvertising redirectors. Attackers injected the ads into videos the sites hosted. These generated pay-per-view or pay-per-click revenue from malvertising platforms and subsequently routed traffic through one or two additional malicious redirectors.
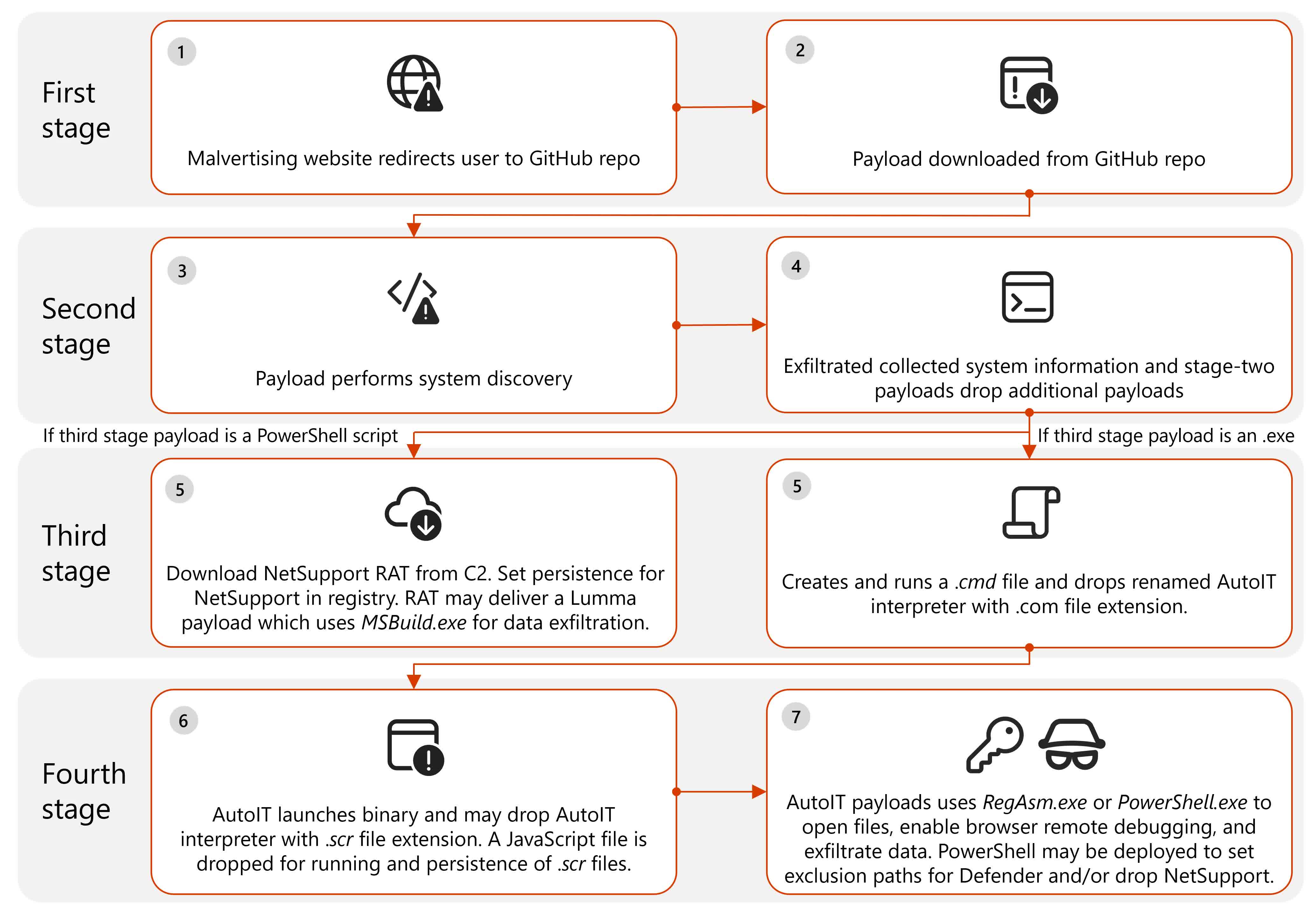
Victims were eventually led to another website, such as a tech support scam website, which then redirected to GitHub.
The GitHub repositories, which have since been taken down, stored malware used to deploy additional malicious files and scripts. Once someone had downloaded the malware, it was used to collect system information and deploy second-stage payloads to exfiltrate documents and data.
A third-stage PowerShell script payload then downloaded the NetSupport remote access trojan (RAT) from a command-and-control server and set persistence in the registry. The RAT could deliver the Lumma information stealer malware or an updated version of the Doenerium infostealer.
The malware also allowed attackers to spy a on victims’ browsing activity and even interact with an active browser, including Firefox, Chrome, and Edge.
The first-stage payloads were digitally signed with a newly created certificate and included some legitimate files to hide their true nature. A total of twelve different certificates were identified, all of which were later revoked.
While GitHub was the primary platform used in the delivery of these payloads, Microsoft also found one payload hosted on Discord and another on Dropbox. As with GitHub, the pages that hosted the malware on these platforms have been removed.
Microsoft writes that the campaign was indiscriminate in nature, impacting both consumer and enterprise devices. It also notes that Windows’ Microsoft Defender software is able to detect and flag the malware used in the attack.